Enterprise IT Resources
Access the latest whitepapers, e-books, and research covering a wide range of topics related to IT innovation, performance, and security.
The Anatomy of DDoS Attacks
The Anatomy of DDoS Attacks: an E-Book by Adapture Detecting and Responding to DDoS Threats When mainstream code exploits and data infiltration fails, some hackers resort to a [...]
Managed Endpoint Solutions
All-in-One Protection for Devices, Data, and People Powered by Avast with the largest, most globally dispersed threat detection network in the world, Adapture Managed Endpoint Solutions deliver superior, enterprise-grade [...]
Building a Well-Architected Cloud
A Comprehensive Guide to the Five Pillars of Cloud If you’re not measuring your cloud performance according to industry standards, you could be leaving your environments open to inefficiencies [...]
Clearing Up the Cloud
A Comprehensive Strategy Guide for Evaluating the Future of Your Infrastructure. “Cloud is better.” You have probably heard this on numerous occasions from varying sources. Yet, peppered within the [...]
How to Plan for a Wireless Assessment
A Comprehensive Guide for Leaders at All Levels. When you hear the phrase “wireless assessment,” a few thoughts immediately spring to mind: daunting, time consuming, labor intensive, and—worst of all—potential [...]
Securing the Cloud
A Comprehensive Guide to Security Best Practices in a Shared Responsibility Model. No one wants to be the next big breach—to get hacked and have private data plastered across [...]
Proactive Cisco Services
Utilize SMARTnet Total Care to Increase Visibility into Your Cisco Environment A Datasheet by Adapture Cisco SMARTnet Total Care makes contract and device lifecycle management more efficient and effective. With [...]
Supporting SHA1 and SHA2 in the Same Virtual Server
Supporting SHA1 and SHA2 in the Same Virtual Server Using F5 Networks’ Local Traffic Manager A Whitepaper by Adapture F5 CTS This whitepaper explains the design behind the support for [...]
Ease Your IT Burden with Intelligent Storage
Eliminate Manual Storage Troubleshooting with AI and Predictive Analytics Today’s IT managers are spending more time managing storage volumes than actually optimizing data for business advantage. With 31% of IT [...]
2021 Guide to Secure Remote Users
How to Improve Collaboration and Secure Network Operations For the Future Over the last year, companies around the globe rapidly deployed remote users with essentially little to no preparation. Following [...]
Shape Enterprise Defense Solution Overview
Prevent sophisticated fraud and cyberattacks on web and mobile applications Web and mobile applications face an onslaught of sophisticated attacks with one commonality; instead of exploiting application vulnerabilities, attackers abuse [...]
Attacker Economics
Understanding Economics Behind Cyber Attacks- What Makes Your Company a Prime Target? Automated attacks are proliferating against organizations around the globe. As the cost and investment of launching these attacks [...]
Credential Stuffing 2021: The Latest Attack Trends and Tools
Understand and Disrupt Sophisticated Attackers Who Retool Against Your Countermeasures From the stereotypical loner in the basement to organized criminal gangs and nation states, attackers have become increasingly sophisticated over [...]
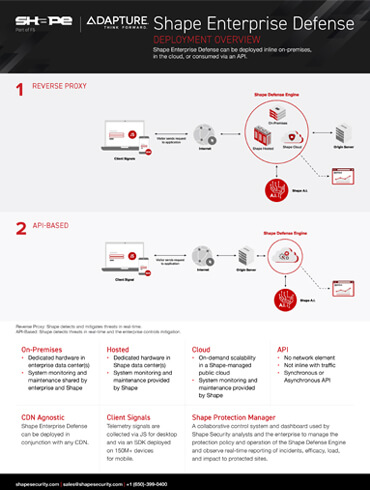
Shape Enterprise Defense Deployment Overview
Shape Enterprise Defense can be deployed inline on-premises, in the cloud, or consumed via an API Fill out the form to the right to download this datasheet and learn exactly [...]
NetApp Data Migration Services Datasheet
NetApp Data Migration Services – Datasheet NetApp offers data migration services to help you get it right the first time. When moving from legacy storage environments, they offer proven methodologies [...]
Security Features in ONTAP 9 Datasheet
Security Features in ONTAP 9 Datasheet With the introduction of ONTAP 9, NetApp has continued to evolve its data management software with security as an integral part. The latest releases [...]
NetApp Cloud Volumes ONTAP Managed Service Datasheet
The world of cloud storage is rapidly evolving. Organizations are moving to the cloud for its robust scalability, flexibility, and agility. As organizations move data to the cloud, they need [...]